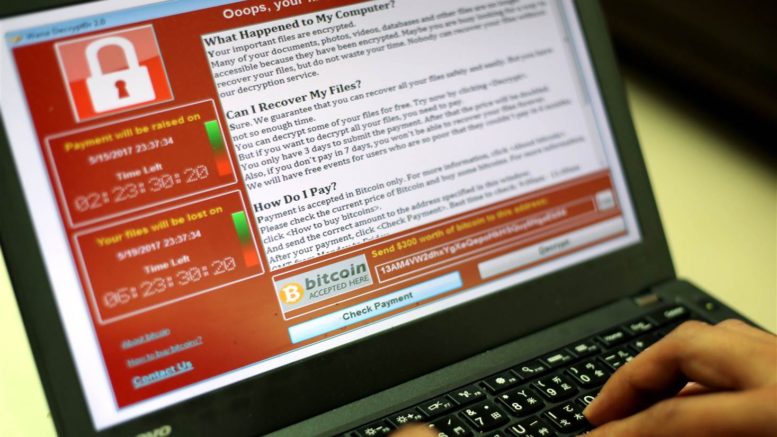
 The WannaCry ransomware attacked with lightning speed across the globe with some estimating it reaching 150 countries and 200,000 systems. Even when researchers discovered a “kill-switch” it didn’t take very long for attackers to create new variants and start up again. Whether ransomware is delivered via e-mail attachment or by leveraging a vulnerability in the operating system, financially motivated ransomware attacks are going to replay themselves multiple times. While ransomware continues to draw attention there are several, valuable lessons that shouldn’t be ignored.
The WannaCry ransomware attacked with lightning speed across the globe with some estimating it reaching 150 countries and 200,000 systems. Even when researchers discovered a “kill-switch” it didn’t take very long for attackers to create new variants and start up again. Whether ransomware is delivered via e-mail attachment or by leveraging a vulnerability in the operating system, financially motivated ransomware attacks are going to replay themselves multiple times. While ransomware continues to draw attention there are several, valuable lessons that shouldn’t be ignored.
Lesson 1: Vulnerability and Patch Management is Essential
The security community has been crying out for decades about keeping computers patched and the WannaCry ransomware campaign clearly shows us why. The rapid spread of this worm was made possible by unpatched operating systems running all over the world. In fact, the patch to protect computers from this attack was released months before WannaCry became a household name. Deploying and keeping out-of-date operating systems in production environments can have devastating effects. Patch. Patch. Patch.
Lesson 2: Unknown Systems Can Bite You
You can’t patch systems you don’t know about. Just “plugging” a computer into an network port because it’s free can have dire consequences. The same goes for unknown computer systems attaching to company wireless networks. This is why a “guest” wireless network should be isolated from the rest of your production network so that a consultant or user connecting with their own, potentially unpatched system can’t infect the rest of your environment. Knowing and managing what systems attach to your network is a basic security measure.
Lesson 3: Network Segmentation Can Be a Huge Risk Reducer
Patch management isn’t as simple as pushing a button. All organizations face legacy and embedded systems that can’t be updated. This is why healthcare organizations were such fertile ground for WannaCry. Some applications require older, vulnerable versions of supporting tools such as Java or you may find that the latest patch breaks the application if it’s applied. If you have known systems that can’t be patched, consider isolating them on a separate network segment as a compensating control.
Lesson 4: Security Has Real-World Repercussions
WannaCry hit the healthcare industry in the UK hard. The lessons here is that cybersecurity is no longer just a game of protecting data and can affect the safety of people’s lives. With devices of all kinds attached to the Internet (healthcare & power monitoring as examples), some can be rendered useless by malware or ransomware. In the UK, people were turned away from healthcare services due to WannaCry. This should send a message that security is not frivolous or even fun. The consequences are very real.
Lesson 5: The Forgotten ‘A’ in the Security ‘CIA’
Organizations get hung up on confidentiality and integrity of data that they overlook availability in the CIA triad of information security. Business interruption often results in lost revenue and increased expense for remediation efforts. It’s easy to focus attention on confidentiality of PII but remember, the availability of systems and services is just as vital and disruption is often a tactic of ransomware and other attacks.
These are big picture lessons and it takes time to turn them into action items. Security is serious business with attacks coming from a variety of angles. It’s important to constantly evaluate, evolve, and grow a security program to continue deflecting the constant barrage of attacks.