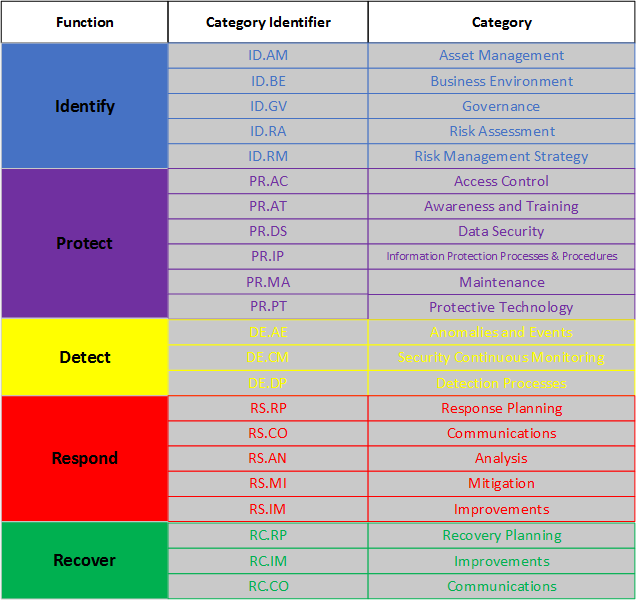
The NSHE Board of Regents have adopted the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) as the basis for implementing, managing, and measuring cybersecurity risk at all NSHE Institutions and System Administration Units. The NIST CSF provides flexibility in the implementation of technical controls and can operate as an overlay for many technical standards and regulatory requirements. Institutions may operationalize controls around standards such as NIST 800-53 or the Center for Internet Security Critical Security Controls which both map to the functions and categories of the CSF.
The CSF itself is not meant as a compliance instrument. That is, there is no checking a box and being done with it. Rather, it is designed to foster continuous improvement based on assessment and prioritization of risk. This is actualized through the development of Current and Target profiles which help lead organizations to a plan of action in developing their security controls. The CSF offers a common language to communicate campus and NSHE’s overall cybersecurity posture with each other and with external stakeholders such as auditors, insurance underwriters and regulators.
This weekly blog series will discuss the different functions and categories of the NIST CSF. It will provide some guidance into what these categories mean and offer, where indicated, some guidance as it maps to the Center for Internet Security Critical Security Controls. Additionally, the blog will offer some insight into potential audit considerations such as the type of evidence that you may be asked to provide.
The functions and categories of the NIST CSF are identified in the chart below. The categories will be explored over the course of several months and can be used as reference as you develop a Current and a Target profile.